Salam Anak IT. Al-kisah...
Pada suatu hari, ada penjual kupi-take-away or nya urang kitani kupi-tapau yang bernama Buajah Lintuk. Setiap pagi, beliau akan menyiapkan kupi-tapau nya dan pergi kerumah-rumah untuk menjual kupi tersebut. Buajah Lintuk akan pergi dari kampung ke kampung untuk menghabiskan jualan beliau.
Pada suatu hari *balik-balik jua* beliau ternampak satu rumah yang agak besar dan "attractive" dengan puluhan mutuka misidis itam bacilat bejuritan dihalaman rumah tersebut. Beliau menghampiri rumah itu dan mendapati pintu utama rumah melayah-layah. Beliau memberi salam namun tiada yang menjawabnya. Beliau berkata di dalam hati "sah inda hada bejelama ni rumah ani..." dan terus melangkah masuk ke dalam rumah tersebut. Beliau ternampak kunci mutuka bertanda "misidis BAA1024.768" di atas mija dapur dan terus mengambilnya. Dengan rasa "gagau ati", beliau terus mencari mutuka misidis yang berdaftar BAA1024.768 diperkarangan rumah itu. Apabila terjumpa, Buajah Lintuk terus membuka pintu mutuka tersebut dan "hooraaayyy inda jua ku lalah bejalan batis menjual kupi ku ane".
Selepas kejadian itu, Buajah Lintuk tidak lagi menjual kupi-take-away dan kini beliau menjual Cappucino-style-melayu di laman jaringan "eBay".

Buajah Lintuk pada waktu sekarang
So... Cuba sama-sama tani pikirkan... If kami yang empunya misidis, apa yang patut disalahkan?...
Mmmm mungkin... But in my opinion pasal RUMAH ATUE PAMPANG-PAMPANG DAPAN MATA... And yes the second reason is pasal rumah atue attractive and melagau-lagau... hahaha "bah miana jua? inda jua kan di gulung kalie rumah atue masukkan dalam pukit seluar?" haha yeah that is true but face the fact that the main reason is pasal Buajah Lintuk nampak rumah atue IN THE FIRST PLACE... Imagine if ia INDA NAMPAK rumah atue... Is she going to enter it? Obviously its a NO... Just imagine peradian kamu cakap "agatah makan nasi katuk atas mija rah dapur ah" then kamu cek INDA ADA. Are you still going to sit down and baca doa sebelum makan? Hahahaha *imagine* and yes in real life, you can't make things INVISIBLE unless kamu ada selimut Harry Potter hehe but what I am going to write today is in CYBER WORLD.
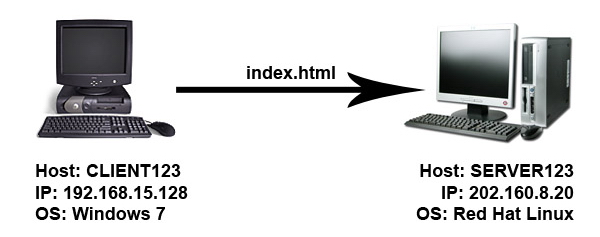
If you want to steal a thing from someone's house,
This method is just the same basic method used by "crackers" or I should say "hackers with bad intentions" in order to steal things from your machine through network,
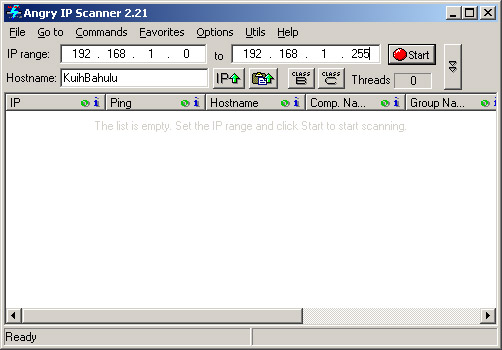
Understood now? So... First, find victim's machine's IP Address. In my previous post, I have wrote on how to check or even tracing IP Addresses using a software named Angry IP Scanner. The software is basically using "ping" method (or other relatively-close technique) to see whether the IP address is alive or not. Actually there are tons of software available on the internet with the same capabilities. If the attacker have got your IP Address and found that it is active and alive, the attacker will proceed to the next stage. So, is there a way to hide our machines from the network? In my case, YES there is.

Original picture was taken from here
This tutorial is specifically for those who runs on Windows XP Operating System. For those who are not using Windows XP, you may just read to understand the technique and then do a research on it based on Operating System that you are using.
Go to Control Panel and click on Windows Firewall,

Click on the "Exceptions" tab and select "File and Printer Sharing",

Click on "Edit..." button,

Select "TCP 445" and click on the box next to it to DISABLE it then click "OK" button

Tadaaaa~ *haha malar* use Angry IP Scanner from other computer within the same network to scan your machine.

BEFORE

AFTER
That is it for today and I hope you gain at least a bit of extra knowledge and awareness. Until next time, sekian. Wabillahi taufiq walhidayah...